The EU cybersecurity regulations introduced in 2016 were finalized by the NIS2 Directive, which came into force in 2023.
In response to these challenges, the Predor access control system has developed the necessary software and hardware infrastructure to meet the requirements at every level. Read on for more details!
Briefly about the NIS2 Directive
For those who are not yet familiar with the NIS2 regulation, here is a brief summary: the directive requires END-TO-END encryption. In the case of an access control system, this means that identifiers, card readers, the data connection between the reader and the controller must all be encrypted. The connection between the controller and the database, as well as the database itself, must also be properly encrypted.
Encryption of Identifiers
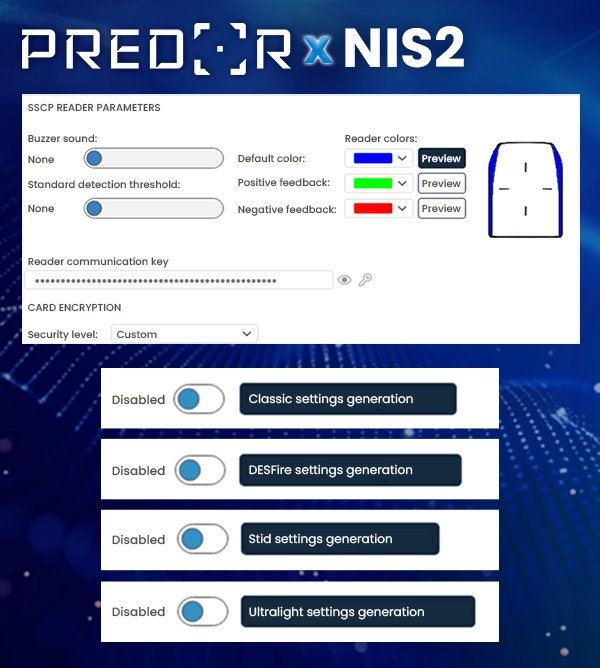
The Predor Enterprise version 1.6.0, with the NIS2 license package, offers four types of card encryption:
1. Mifare Classic – Low security level, easy to hack and duplicate.
2. Mifare DESFIRE – AES 128 encryption, high security level — ideal for maximum protection!
3. STid mobile ID – A green virtual card that can be used for free via a mobile application.
4. Mifare Ultralight – Low security level.




When selecting identifiers, always keep in mind that access control systems are most often targeted first through the devices used by end users. Therefore, by increasing the security level of these devices, we make it more difficult—or even impossible—for unauthorized individuals to gain access to protected areas.
Encryption of Card Readers
- First step
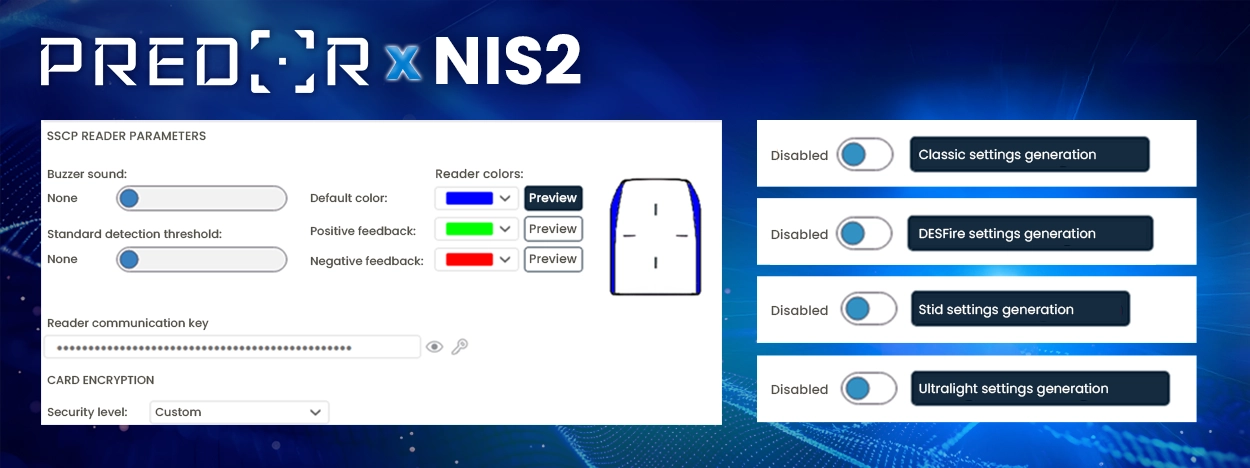
From the STid card reader range, only readers capable of SSCP V2 communication can connect to the Predor Phantom controller. For encrypted communication, the SSCP module attached to the Predor Phantom panel is essential, as it converts the inputs of Wiegand readers into encrypted RS-485 signals.






By purchasing the readers, we have only ensured the first pillar of encryption – these Stid card readers are no longer the well-known, simple Wiegand readers. Here, communication is already two-way: the controller monitors the reader and applies encryption! But of course, this only happens if we have properly configured it within the Predor software – this is where the second pillar of encrypted readers comes into play.
Encryption of Card Readers
- Second step
The next stage of encryption is the Predor Phantom controller panel itself. It integrates the hardware components mentioned so far and transmits the data to the server over an encrypted channel. The AES128 encryption used here also meets the NIS2 requirements.
The full functionality is truly realized in the Predor Enterprise 1.6 client software, which allows us to customize the essential features. The software designers have structured the menus so that, with proper configuration, the system is practically self-operating and eliminates potential human error factors.


The Predor access control system’s NIS2 license package is just one of its many useful features. At this level, we are no longer talking about a simple access control system; it is more appropriate to refer to it as an ecosystem.
If you need more information or would like to request a quote, please contact your Sales Representative or our Technical Team at the following email address: muszaki@powerbizt.hu.